Network Testing & Validation Solutions


Valid8 provides a flexible, affordable solution to specific problems covering Feature, Conformance, Emulation and Load Testing for 5G, LTE/4G, 3G, IMS, VoIP and PSTN telecommunication networks. Valid8’s 'Protocol Engine’ has a scalable architecture based upon COTS Server Hardware. The application software has many features to streamline telecommunications & network testing and can be customized according to the customer’s environment allowing the user to run a variety of tests and modify the software to meet future testing needs.
Emulate Any Interface In The Network
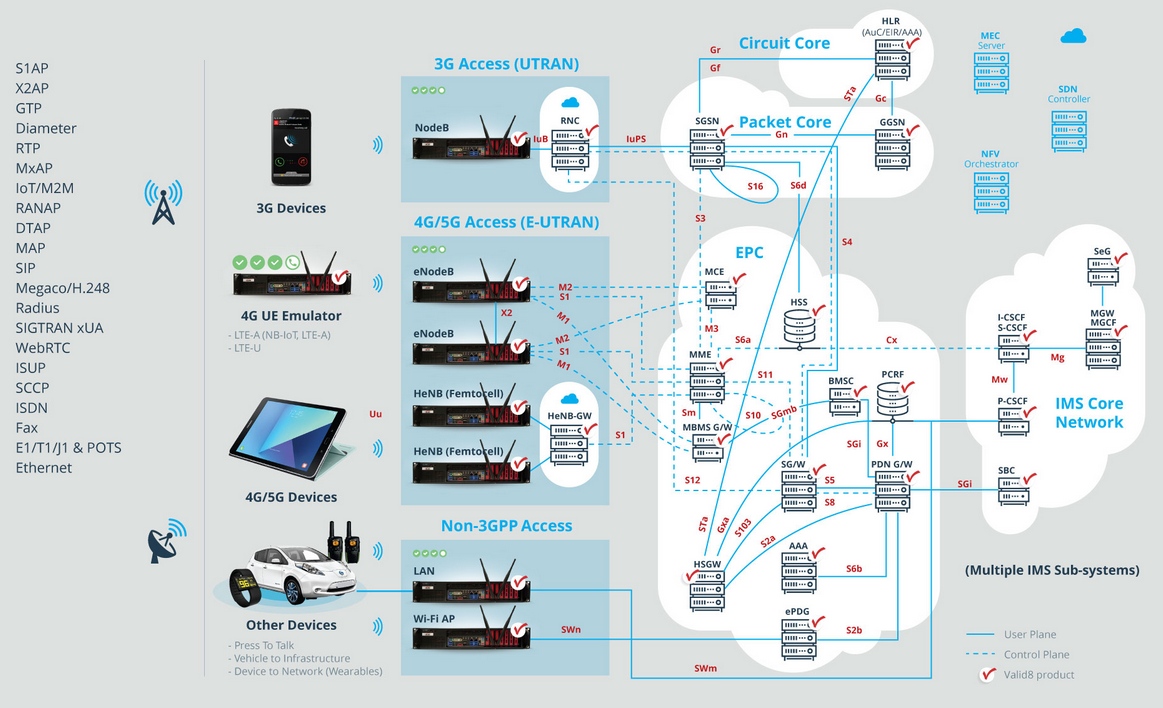
Valid8's network test applications are built on their unique ‘Protocol Engine’, a scaleable and powerful platform providing customizable Telecom/Network Testing solutions for a wide variety of emulation and load testing functions such as Device and network emulators, Call traffic load generators, QoS testers (Quality of Service), Feature testers, Conformance testers, Protocol traffic analyzers, Negative testing.
This comprehensive testing suite supports a broad range of protocols, including the following:
Applications: 5G Network Emulator 5G Network Emulator
Protocol Details
The 5G Network Emulator provides an all-in-one, cost-effective and ultra-portable 5G network for demonstration, testing and training purposes. It can emulate 5G core network nodes and generate realistic traffic between network devices by supporting the following features:- Emulates some or all of core network, exposing all internal interfaces
- Conformance tests available for each interface
- Emulators available per subsystem
- OTA connection available for UEs and IoT devices
- True stateful simulation
- Handover support on X2 and S1
- Signaling request/response messages for call handling, mobility management, authentication, QoS
- Report on media received, call connect time, call duration, jitter, packet loss
- Generate valid and invalid/negative messages and call-scenarios (fully editable scenarios)
- Supports sending invalid messages including malformed, dropped, and misordered packets
- Check parameters in messages from SUT and flag errors
- 3GPP-compliant interfaces
Applications: Internet of Things IoT Load Tester
Protocol Details
The Internet of Things (IoT) Load Tester provides an all-in-one, cost-effective solution for emulating and testing against large numbers of IoT devices. It is a fully automatable solution that addresses the unique challenges brought by IoT testing by supporting the following wide ranging features: manufacturers:- Ability to simulate an entire city’s worth of IoT devices!
- Supported protocols include CoAP, MQTT, HTTP REST, XMPP, and custom protocols
- Cross-domain protocol support
- Fully automatable using HTTP REST API
- Alerts and notifications
- Scalable architecture
- True stateful simulation / deterministic behavior
- LTE -U/-N support
- Network impairment simulation
- Generate valid and invalid/negative messages and scenarios including malformed, dropped, and misordered packets (fully editable scenarios)
- Signaling request/response messages for handling, mobility management, authentication, QoS
- Check parameters in messages from SUT and flag errors
Protocol Details
Mobile Network Testing solutions for LTE, UMTS and GPRS. Rapidly test & troubleshoot 4G, 3G & 2.5G networks with Valid8's Protocol Engine test solution for Wireless.Applications:
Fixed Network Testing
Protocol Details
Fixed Network Testing - VoIP, SIGTRAN and PSTN Testing. Rapidly test & troubleshoot fixed networks:- AS-SIP Feature Tester
- BICC Load Tester
- DHCP Load Tester
- Diameter Load Tester
- ISDN Load Tester
- Megaco Load Tester
- Radius Load Tester
- WebRTC Conformance
- WebRTC Load Tester
- Wireline Conformance
Network Security Testing
• Tools to generate realistic, stateful traffic to help detect vulnerabilities
• Pre-canned conformance test suites to verify the network protocol stack implementations are correct and protected
• Complements Denial Of Service (DOS) tools
• Lab or cloud based solutions to run traffic generation services from outside an organisation's own network
• Ability to spoof MAC/IP and geographic location of where the simulated data comes from
• Stress testing, loading past the specified limit of the device under test (DUT) to see where it breaks
• Ability to create and test with invalid / unusual flows / messages
• Same test environment and language for many protocols and domains
• Easily tied into automated environments for regression testing etc
• Benchmarking – no of calls and call statistics etc
• Simulate malicious phones and networks





